UNIT 4 SEARCHING THE INTERNET
Introductory activity 4.0
During the end of the year holiday, Jean Claude, a student in Senior Four in one
of the schools with Associate Nursing Program in Rwanda received a message
from someone claiming to be a girl who studies in Senior Four at the same
school. The girl claimed to have feelings for Jean Claude. They chatted as much
as they could even confidentially and sent to each other pictures.
At the beginning of the new school year Jean Claude met the girl as they entered
the school gate and tried to hug her but the girl seemed not to know him. Later
he learned from her that they never chatted. Some weeks later Jean Claude
received a message that if he does not pay 100000 Frw his nude pictures will be
published on social networks.
a. “The girl seemed not to know him” Explain why while they introduced
themselves to one another and have been sending pictures to one another
b. Discuss how Jean Claude would have prevented the threat of having his
nude pictures shared
c. Have you encountered a problem like this while using the internet and
social media? Discuss.
4.1 Internet ethics
Activity 4.1
During the end of the year holiday, Jean Claude, a student in Senior Four in one
of the schools with Associate Nursing Program in Rwanda received a message
from someone claiming to be a girl who studies in Senior Four at the same
school. The girl claimed to have feelings for Jean Claude. They chatted as much
as they could even confidentially and sent to each other pictures.
At the beginning of the new school year Jean Claude met the girl as they entered
the school gate and tried to hug her but the girl seemed not to know him. Later
he learned from her that they never chatted. Some weeks later Jean Claude
received a message that if he does not pay 100000 Frw his nude pictures will be
published on social networks.
a. “The girl seemed not to know him” Explain why while they introduced
themselves to one another and have been sending pictures to one
another
b. Discuss how Jean Claude would have prevented the threat of having
his nude pictures shared
c. Have you encountered a problem like this while using the internetand social media? Discuss.
Internet is an interconnection of computer networks worldwide providing a series of
information and communication facilities and thus being a big tool for carrying out
researches.
Internet ethics refers to set of moral principles that regulate the use of internet.
Thus the internet users must be honest, respect the right and property of others on
internet.
The following are ethical issues that should be addressed at individual, social, and
political level:
a. Flaming
Flaming refers to messages that contain offensive, obscene or immoral words
spread via social media applications such as WhatsApp, Facebook and Instagram.
b. Forgery
Availability of computers and high-resolution imaging devices has made it possible
for criminals to forge certificates, money and identity cards.
c. Piracy
Piracy is a form of theft of intellectual property on copyrighted software products
without proper authorization. To avoid violation of copyright laws, everyone needs
to understand various software licences.
d. Terrorism
High penetration of internet and mobile phones has exposed most countries to evil
plans of terrorists across the globe.
e. Pornography
Availability of pornographic material in form of pictures and video has affected
moral values of young children leading to immoral behavior such as homosexuality
and premature sex.
f. Fraud
Computers and mobile phones are being used to steal other people’s account details
or money through fraudulent means such as fake websites and SMS messages.
g. Corruption
Corruption has become social evil in private and public institution because it is
seen as the easiest means to gaining social, economic or political favors. In some
countries, mobile and internet-based money transfer has opened doors to corrupt
behavior that goes unnoticed by law enforcement agents.
h. Blackmail
Is an action of asking money or any other benefits in exchange to not revealing
private information on someone. That information can be nude pictures or videos
and other compromising information about someone.
As internet ethics mean acceptable behavior of using internet below are ten rules
that anyone using the internet should follow:
1. Do not use the Internet to harm other people.
2. Do not interfere with other people’s internet work.
3. Do not snoop around in other people’s internet files.
4. Do not use the Internet to steal.
5. Do not use the Internet to bear false witness.
6. Do not copy or use proprietary software for which you have not paid without
permission.
7. Do not use other people’s Internet resources without authorization or proper
compensation.
8. You shall not appropriate other people’s intellectual output.
9. Think about the social consequences of the program you are writing or the
system you are designing if it is to be used over the internet
10. Always use the Internet in ways that ensure consideration and respect for
your fellow humans
Apart from the rules some of the ethics to be followed while using internet are here
below:
• While using email and chatting, internet must be used for communication or
for research purpose. Be on guard while chatting with stranger and avoid
forwarding e-mail from unknown people or stranger
• Do not be rude and do not use bad language while using email, chatting,
blogging and social network, be respectful to others’ views.
• It is not advisable to use internet to fool others or pretending to be someone
else, hiding one’s identity to fool other on internet is a crime.
• It is not advisable to download and share the copyrighted material without
permission.
APPLICATION ACTIVITY 4.1
1. Brainstorm on how technology use has influenced our morals in terms of
communication, privacy and intellectual property rights.
2. What are ethical challenges arising from the use of computers and mobile
devices used to access the internet?
4.2. Web security spyware, hacking and firewall
Activity 4.2
1. Discuss the measures taken by your school to protect computers against
different security threats If they are not secured suggest solutions that can
be used to safeguard them
2. By doing a research write down some cases of internet security break thathave happened in Rwanda and in the world?
Computers are indispensable tools in the life of human beings. Computers are
used in different area such as banking, shopping, communicating between people
through emails and chats, etc. However, some intruders join the conversations
and try to read emails and other information for which they don’t have the rights.
Most of the time, they misuse their computers by attacking other systems, sending
forged emails from computers, or examining personal information stored in others’
computers.
Web security, spyware, hacking and firewall are among the terms that are
common in the world of internet specifically when it comes to using the internet.
The common attributes for all these terms are that they refer to the need to use the
internet securely.
4.2.1. Web security
Web security refers to the techniques of protecting computers, networks, programs
and data from unauthorized access or attacks. Major areas covered in web security
are: Application Security, Information Security, Disaster recovery and Network
Security.
The key Web services security requirements are authentication, authorization,
data protection, and no repudiation. These are implemented in order to have
more security while on the web.
a. Authentication
It is a process in which the credentials provided are compared to those in the
database of authorized users’ information on a local operating system or within
an authentication server. If the credentials match, the process is completed and
the user is granted authorization for access. Therefore, authentication verifies the
identity and enables authorization.
b. Authorization
The term authorization is the process of giving someone permission to do or have
something. In the field of computer an authorized user gains access to the system
and is allowed to get the available resources depending on the access level attached
to his/her credentials.
c. Data protection
It is the process of safeguarding important information from corruption, compromise
or loss.
4.2.2. Spyware
Like virus, Spyware also comes under the category of malware attacks. Although
the working of spyware is different from the other types of malware mentioned
earlier in unit 2, Spyware as the name suggests is used to spy into a system. The
job of the spyware is to silently sit inside the host system and observe the activities
of that system.
i. How spyware work
Suppose a user is logging on to any bank. Once the website of the bank opens, the
user id and login password are input. After that if the user wants to do a financial
transaction, the transaction password has to be entered. All this information is quietly
registered by the spyware then the spyware sends all the information recorded from
the user’s computer to probably a hacker who is somewhere else on the Internet.
ii. How spyware is spread
Devices which use windows operating systems are more susceptible to attacks;
here below are the most common ways, a computer can become infected with
spyware:
• Accepting a prompt or pop-up without reading it first
• Downloading software from an unknown source
• Opening email attachments from unknown senders, etc.
iii. How to recognize spyware on the device
Spyware can be difficult to recognize in an infected device. But there are clues
that can help one to know that a computer has been infected. The symptoms
of a computer attacked by a spyware are that the device is so slow or crashes
unexpectedly, it runs out of hard drive space and there are pop-ups when online or
offline.
iv. How to remove spyware
If the device is infected with spyware, it is necessary to run a scan with current
security software to make sure it has cleaned up everything it can. The best fight
against a spyware is to install reputable anti-spyware removal tools.
v. How to help prevent spyware
Here are four main ways to help prevent spyware.
Do not open emails from unknown senders.
• Do not download files from untrustworthy sources.
• Do not click on pop-up advertisements.
• Use reputable antivirus software.
4.2.3. Hacking
Hacking is a term used to describe actions taken by someone to gain unauthorized
access to a computer belonging to other people. It is the process by which cyber
criminals also known as hackers gain access to a computer. After entering in that
computer, a hacker can find weaknesses (or pre-existing bugs) in the security
settings and exploit them in order to access available information. Hackers can
also install any malware such as spyware or Trojan horse, providing a back door in
where to enter and search for information.
4.2.4. Firewall
A firewall is a network security device that monitors incoming and outgoing network
traffic and permits or blocks data packets based on a set of security rules. Its
purpose is to establish a barrier between an internal network and incoming traffic
from external sources such as the internet in order to block malicious traffic like
viruses and hackers.
i. How does a firewall Work ?
Firewalls carefully analyze incoming traffic based on pre-established rules and filter
traffic coming from unsecured or suspicious sources to prevent attacks. Firewalls
guard traffic at a computer’s entry point, called ports which is where information is
exchanged with external devices.
ii. Types of Firewalls
Firewalls can either be software or hardware, A software firewall is a program
installed on each computer and regulates traffic through port numbers andapplications, while a physical firewall is a piece of equipment installed between the network and the gateway.
APPLICATION ACTIVITY 4.2
1. Discuss and write a brief report on the importance of web security at your
school, in Rwanda and in the whole world.
2. In a bank, any customer can create and use an identity (e.g. a user name
and password) to log into that bank’s online service but the bank’s policy
must ensure that the customer can only access individual account online
once his/her identity is verified.
a. Identify which type of security is used in this bank?b. Why is that imposed security important?
4.3. URL and its partsActivity 4.3
Each year all students of P6, Senior three and Senior six pass the national
exam. Marking is the second step that follows. After marking, Rwanda Basic
Education Board avails the result on its web application so that each student
can view the results. Give and explain the steps to go through for accessing
national exam results
1. Briefly explain the term web browser
2. Differentiate between a web page and website as used when referring to
the internet
a. Web browser
Commonly referred to as a browser. It is a software program that allows a user
to locate, access, and display web pages. They are used primarily for displaying
and accessing websites on the internet as well as other content created using
appropriate languages such as Hypertext Markup Language (HTML) and Extensible
Markup Language (XML).
Examples of browsers: Mosaic, Netscape Navigator, Internet Explorer, Mozilla
Firefox, Opera and Google Chrome.
b. Website
It is a collection of related web pages stored as a single file in a web server. It is also
defined as a group of World Wide Web pages usually containing hyperlinks to each
other and made available online by an individual, company, educational institution,government, or organization
c. Webpage:
This is hypertext and hypermedia documents containing information about an
individual or organization. It is accessible through the internet or other networks
using an internet browser.
A web page is accessed by entering a URL address and may contain text, graphics,
and hyperlinks to other web pages and files.
4.3.1. Uniform Resource Locator (URL)
The term Uniform Resource Locator abbreviated as URL commonly known as
website address is a unique address of each web page and identifies the location
of that specific web page on the internet. An example of URL is: http://www.yahoo.
com
4.3.2. Parts of URL
The URL consists of three main parts namely: Protocol, Domain also known as host
name and Resource ID.
i. Protocol
It is a set of rules that governs how data is transmitted over a network. There are
many types of protocols used in a network. In a URL address, the protocol is shown
at the beginning of the address followed with a colon and double slashes. In the
example above the protocol is http (Hypertext Transfer Protocol).
Nowadays, HTTPS, which stands for Hypertext Transfer Protocol Secure, is the most
common used protocol. It tells a web browser to encrypt any information entered
onto the page, like the passwords or credit card information, so cybercriminals
cannot access it.
ii. Server name or Host name
It identifies the computer on which the resource is located. This computer is known
as a remote server. Most web server names begin with the letters www (For
example www.igihe.com)
The server name always ends with a dot and a three or two-letter extension called
the domain name.
iii. Domain name
The domain is important because it usually identifies the company, agency or
organization that is directly responsible for the information, or is providing the
computer space where the information is kept. Sometimes it indicates the country
where the server is located.
The Top-Level Domain (TLD) specifies what type of entity an organization registers
as on the internet. For example, “.com” is intended for commercial entities. Here
below are some common top-level domain names:
• com: identifies company or commercial sites.
• org: for non-profit organization sites.
• ac: for academic/educational institution.
• edu: for educational sites.
• go: for government agencies sites.
• net: for Internet service providers.
• co: for company.
• mil: for military organization.
Examples of country domains are .rw for Rwanda; .ke for Kenya; .uk for United
Kingdom; .jp for Japan; .tz for Tanzania; .us for United States; .au for Australia; .ca
for Canada; etc.
iv. Sub domain
Website is like a house; sub domains are like specific rooms in that house. A sub
domain in a URL indicates which particular page of a website the web browser
should serve up.
v. Resource ID
It identifies the file name and the folders or subfolders under which the webpage is
stored on the remote server.Example of resource ID is /index.php/ icons/services
APPLICATION ACTIVITY 4.3
1. What do you understand by the term web address
2. Describe all parts of URL3. What do mean by the term Top level domain?
4.4. Search on the internet
4.4.1. Strategies for better search results:
4.4.1.1. Simple search techniqueActivity 4.4
1. Considering the image below of Google search engine window. Name theparts labeled from A to G
2. Open the browser in address bar, type the most used search engine and in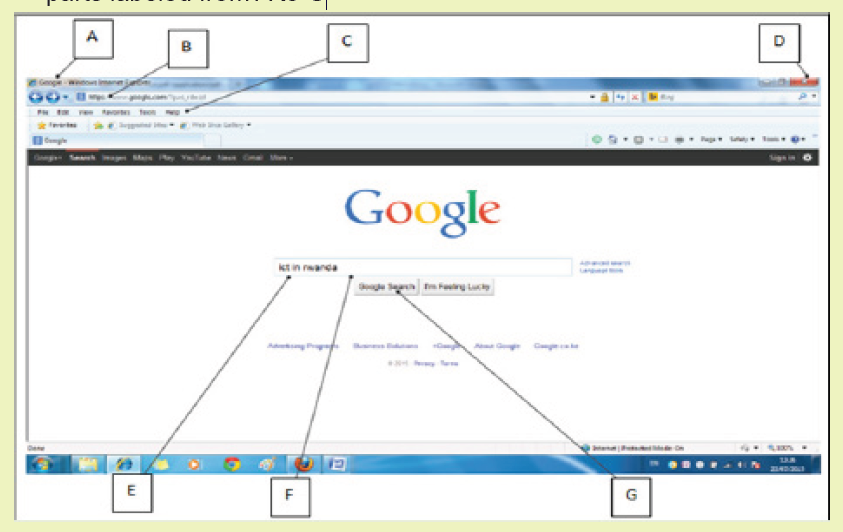
search box type the following text “the proper use of ICT in Rwandan school”Explain what you observe after
Search on the internet requires the use of search engines, such as Google or Ask.
The words that are typed in the search box are called keywords, and should be
directly related to the topic that one is searching for.
Understanding how to perform searches for online information increase the chances
of finding the needed information.
Search Engine: Search Engines are programs that help the user look for and
identify items that corresponds to keywords or phrases specified from the World
Wide Web. Examples include; Yahoo, Google, Bing and Ask.com among others.
A. Strategies to pinpoint specific information online
Searching the internet can be a frustrating; researcher may enter a word or a phrase
into a search engine and get irrelevant information. What is need is the ability to
refine the search to get exactly what is needed.
1. Vary the Search Engine
Search engines search through about millions of active websites to provide content
and source of content. No search engine is perfect, they all have shortcomings that
are avoided only by the techniques of the user while searching.
Keywords are the terms that searcher uses to find content on the internet. Making
the keywords as specific as possible will lead search engine to track down the
information that user needs.
2. Simplify the Search Terms
Some engines include Stop Words in their searches. These are frequently used
words such as prepositions (in, of, on), conjunctions (and, but) and articles (a,
the), which means that the search results have more pages of search results than
needed.
It is usually best to eliminate stop words from the internet searches. The main
exception is if the search is based on looking for a specific title or name that includes
them.
3) Use Quotation Marks
Enclosing a search term also known as search query within quotation marks
prompts the search engine to search for that specific word or phrase.
If the term is a single word, using quotation marks will cut out stemmed variations
of it. For example, if searching for the word director, the researcher likely receives
a lot of results for direct, direction, directions, and so on typing “director” with
quotation marks, ensure that only results for that stem word are displayed.
If the search term is a phrase, the search will be for that specific phrase, rather than
for all the component words as individual items. For example, if searching for the
phrase director of human resources, without quotation marks, the search returns
results based on all of the words in the phrase. Thus, surrounding the term with
quotation marks, will generate results that feature this specific term.
4. Remove unhelpful words
The use of a hyphen, small dash or minus sign immediately before a word excludes
it from a search.
For example, typing in marketing -digital will exclude digital from the search
engine, making it easier to find the information searched for. Typing marketing
-digital -social would allow researcher to get rid of even more confusion.
5. Refine the search using operators
Other characters or terms, known as operators allow to narrow down the internet
search in more targeted ways. A few of those are explored here below:
• Wildcard searches: use the * symbol as a placeholder for another word. For
example, searching for * man in the world returns results for the richest man
in the world, the tallest, the oldest, and so on. Wildcard searches are also
useful for example when researcher do not know the full text of a quote.
• Combination searches: the OR operator enables user to search for two or
more terms simultaneously, and is most useful when those terms are very
similar. For example, typing selling OR retailing, will return pages where
either of the terms is used, without both needing to be present.
• Another way to combine searches is to use AND. This operator ensures that
researcher receives only search results that include two or more terms.
• Search in a specific Site: Typing the site followed by the URL of the website
that researcher wish to search and a search term limit the search to a single
website. For example, the site: reb.rw” Director General” will return all the
pages from reb.rw that feature the term “Director General.”
• Finding related sites: A useful operator is related. Typing this in front of a web
address like in the search sentence “related: igihe.com” (don’t consider the
quotes) will deliver a range of websites that are similar to igihe.com.
6. Avoid the use of difficult word to recognize (Search Pitfalls)
Note: When searching online, it is important to bear in mind that the use of
abbreviation cannot give the relevant result.
Whatever written in search box of search engine, the search engine tries to provide
relevant information related to the search query. The window below shows what
the search engine displays when researcher wants to get information about currentRwandan District
B. Keywords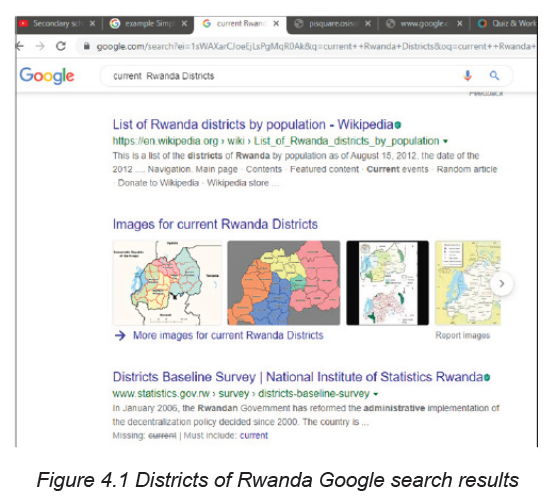
Keywords are the words that the search engines use to find pages. Generally, the
more specific the word, the better the returned results will be, because the page
which contains that word will more likely have something the user intended to look
for.
APPLICATION ACTIVITY 4.4
1. Using Google search engine conduct a research about the topic” IMPACT
OF GIRA INKA MUNYARWANDA”
2. Using Search in a Specific Site, Conduct a research about the all prime
ministers of your country .
4.4.1.2 Advanced search techniques
Activity 4.5
1. Conduct a research on internet about Boolean operators
2. Using different search techniques which include Boolean operators,
quotation marks,… do a research on the internet about the sexual
development of a human from birth to adolescence .
i. Advanced search techniques using Boolean operators
Boolean searching, also known as searching using Boolean Operators in between
the search words is the single most effective advanced search techniques used to
improve the search results, making them more relevant and precise. While using
these operators capitalize the words AND, OR, and NOT to form the most effective
search queries. Additionally, quotations are important when searching for a phrase
or multiple phrases.
Examples:
• Keyword1 AND Keyword2: Results must include both results
• Keyword1 OR Keyword2: Results must include at least one of the keywords
• Keyword1 NOT Keyword2: Results must exclude Keyword2
The Boolean logic expression “Lesson and Tutorial” once typed in search engine
will ensure that the engine returns document which contains both words.
The Boolean logic expression “power imbalance” OR “power balance in
mediation “once typed in search engine will ensure that the engine returns any
document which had either of the terms.
The Boolean logic expression “Lesson Not Tutorial” once typed in search engine
will ensure that the engine returns any document which contains Lesson but nodocument contain the word Tutorial will appear in the same page of search engine.
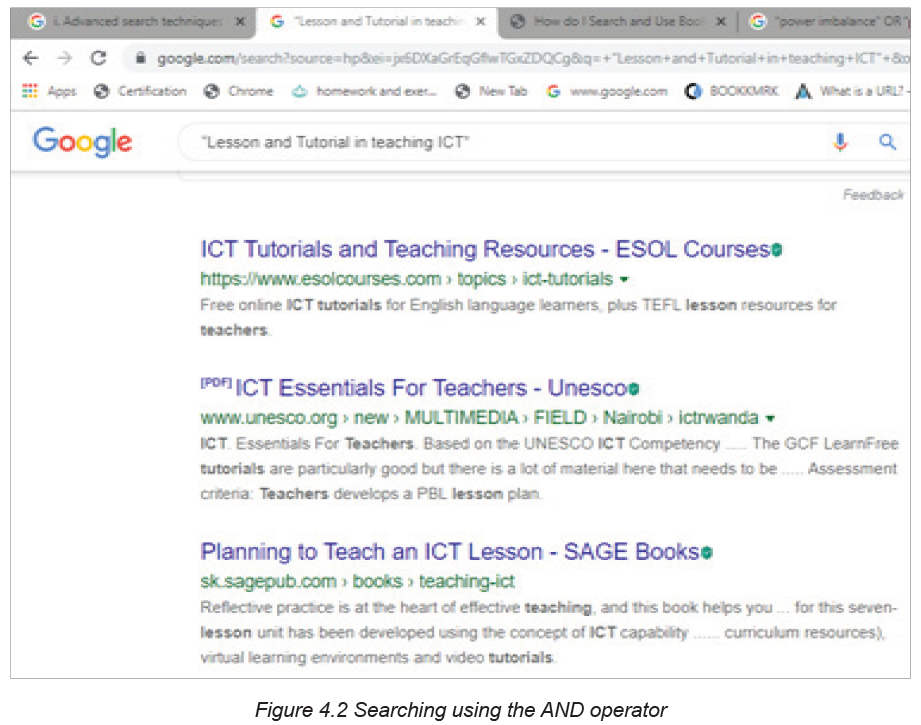
When the AND operator is used in the search query, the search engine returns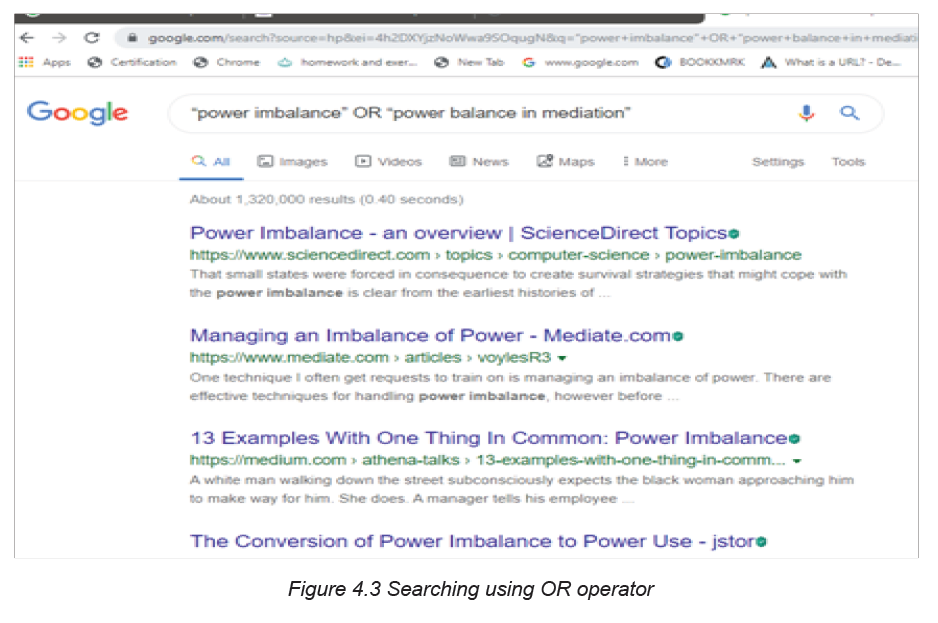
results whose content has both keywords on either side of the operator. In this case
the words lesson and tutorial will appear in the search results. On the other hand,
using the OR operator will return only results containing one of the operand words.
Note: both or none of the keywords may not appear in the search results when
the operator AND, OR are used but when the link is opened the opened page will
contain those keywords
ii. Advanced search technique using quotation marks
Quotation marks (“”) can be used in search engine to avoid finding similar terms
or derived words. They are used around phrases. The use of quotation marks tells
the search engine to only bring back pages with the typed term in exact order they
were typed.
Example: typing the “health and care reform” in search engine is accurate than
typing health and care and reform and will display in the search results that
sentence in quotes
iii. Advanced search techniques using tilde sign (~)
When the tilde operator is placed in front of a keyword, it also searches for words
that are synonyms of that keyword. The searcher can use the tilde operator (~) to
get Google or other search engines to expand the search with related keywords.
This is helpful when one does not know the entire search query to use.
iv. Advanced search technique using NEAR
This operator is a more specific form of the AND operator. It ensures that the
document contains both terms and that they are located near each other. In many
lengthy documents, just using the operator AND might not provide useful results as
the two keywords might be located in very different parts of the document and might
not be related to one another.
Example: The expression “resistance NEAR physics” used in the field of physics
search engine will ensure that the engine uses both words in its search and ranking
logic that both words appear
v. Advanced search techniques using parenthesis
The operators AND, NEAR, OR and NOT are powerful in their own right but when
used in conjunction with parentheses, they can offer substantial control over the
search logic executed by the engine. Parentheses are used in Boolean logic
similar to the way they are used in mathematical equation, limiting and ordering
relationships between variables.
Example: If one wants to find a web-based internet tutorial, it is better to use the
search criteria internet AND (tutorial OR lesson). The documents returned must
contain both of the word internet and tutorial or internet and lesson. Obviously, the
parentheses are used to distribute the keyword internet to one of the two “OR”
words inside the parentheses.
APPLICATION ACTIVITY 4.5
1. Using the advanced search techniques seen, search on the internet about
these topics:
a. Non-renewable energy
b. The power of the mind
3. Discuss about the use of NEAR keyword used in advanced search
techniques
4.4.1.3. Searching for documents, books, images, video on the
internet
Activity 4.6
1. One day an ICT teacher wanted to teach about the topics “assembling
and disassembling computer”. The day before the teacher gave homework
to the students to go to the internet and watch for video showing how to
conduct the activity to assemble and disassemble computer.
a. Suppose you are in that class, search for those videos on the internet
b. Analyze the videos got and compare them in terms of their relatedness to
the topic
Finding specific information on the internet is compared to searching for information
in the library. It is not necessary to have experience in internet searching or even to
know where to locate search sites. Different ways of searching for document, books
and video on internet are elaborated in the sections to follow.
A. Searching for documents
Most information is found on the internet by using search engines. While searching
for documents online using search engine simply require the typing of search query
in search box, the search engine displays a lot of information which can be in
millions of pages like in the image below where more than 6 millions of pages arereturned.
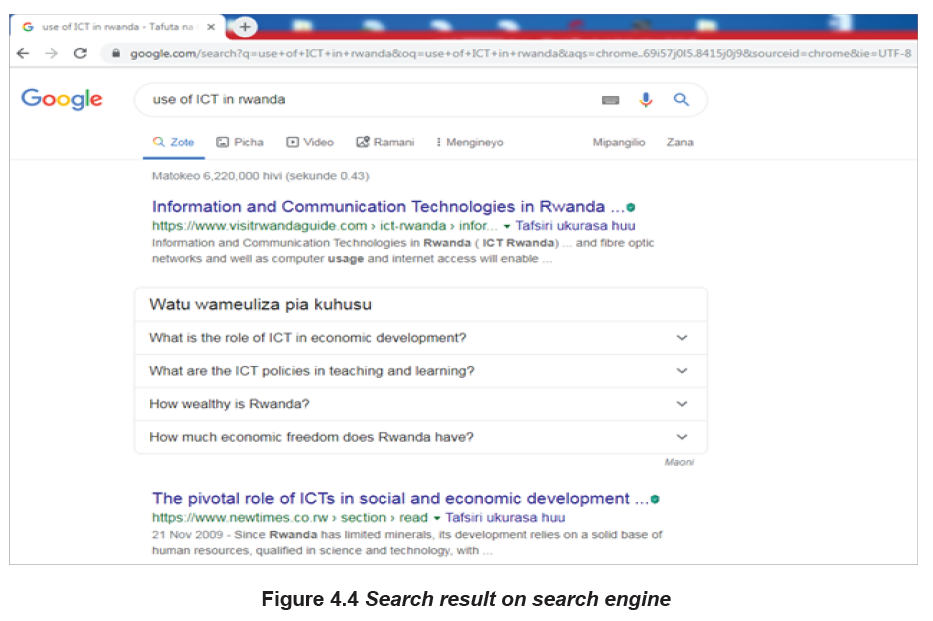
Accessing document from internet
The process of getting files from the internet is known as downloading. The
downloaded files can be viewed, saved or printed. Any attachment sent in an
internet needs to be downloaded.
The process of putting information, document, web pages, images and files onto a
web server is also known as uploading
B. Searching for book
There are different ways to search for online book such as using Wikipedia,
Google as search engine; researcher can even search for books which have been
uploaded to any site such as in-house books uploaded to the REB website. When
the searched book is found, the next step is to download it.
To search for a book using Wikipedia, one needs just to know the book Title, Author,
publication house, and date of publication for that book.
There are free online websites such as www.free-ebooks.net but also there are
some websites where books are found after payment. Those websites are like
amazon, barner and noble.
C. Searching for images
Most people use the web to search for images. They like to search for images
online and there are many sites and search engines dedicated just to searching
different kinds of images. While searching for online images consider the copyright
issues before using them.
To search and download images from the internet follow these steps:
1. Type “google.com” in the web address to find the image to download.
2. Type the name of the image needed, in the available list of related images
select the needed image.
3. Right-click to the image to save.
4. Click Save image as, searcher can even use “copy image as” option.
5. Choose location where to save the image.
D. Searching for video on the internet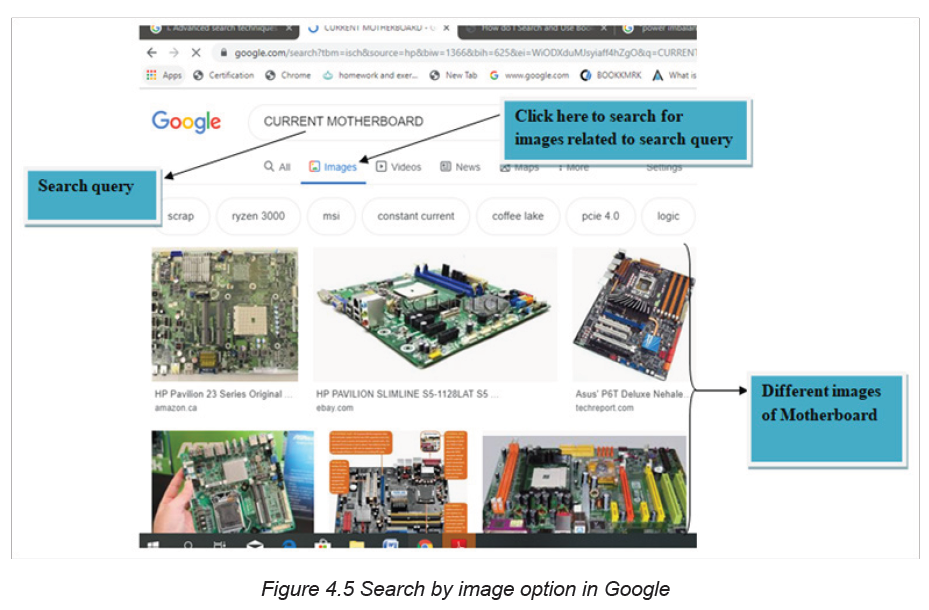
Internet video or online video is the general field that deals with the transmission of
video over the internet. Internet video exists in different formats, such as MPEG-4
AVC, AVCHD, FLV, and MP4 MP, MP4A etc. Those videos can be accessed through
several online video hosting services, such as YouTube, as well as Vimeo, Twitch,
and Youku, vid mate etc.
D.1. Searching for video using search engine and video icon
It is easy to access videos through the use of video icon located on search engines.
The process of locating videos simply requires to type the name and the author
of the video in search box of search engine and thereafter click on video icon asshown in the figure below:
D.2. Search video on internet using online video hosting services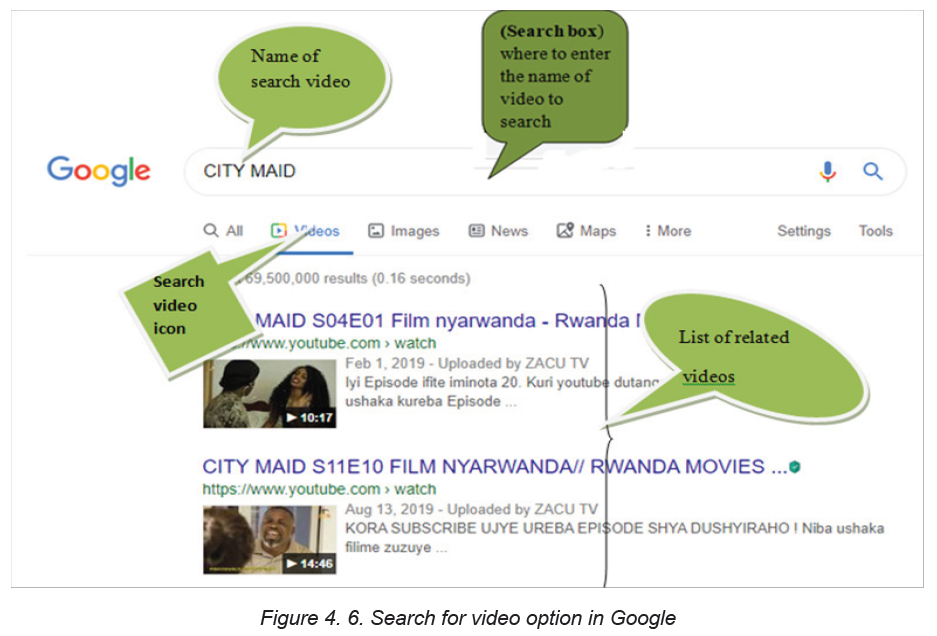
Internet video or online video such as YouTube, vimeo, Twitch, and youku, vidmate
for Smartphone are very useful tools that help to search for video.
To search for video online proceed as follows:
• Open the browser
• In web address or URL type the online video hosting services such as youtube.com
• In the opened webpage just write the name of the video by specifying its
author in order to avoid confusion.Here is a window showing how to find a video using YouTube online hosting service.
Once a video is seen it can be watched online or downloaded and saved using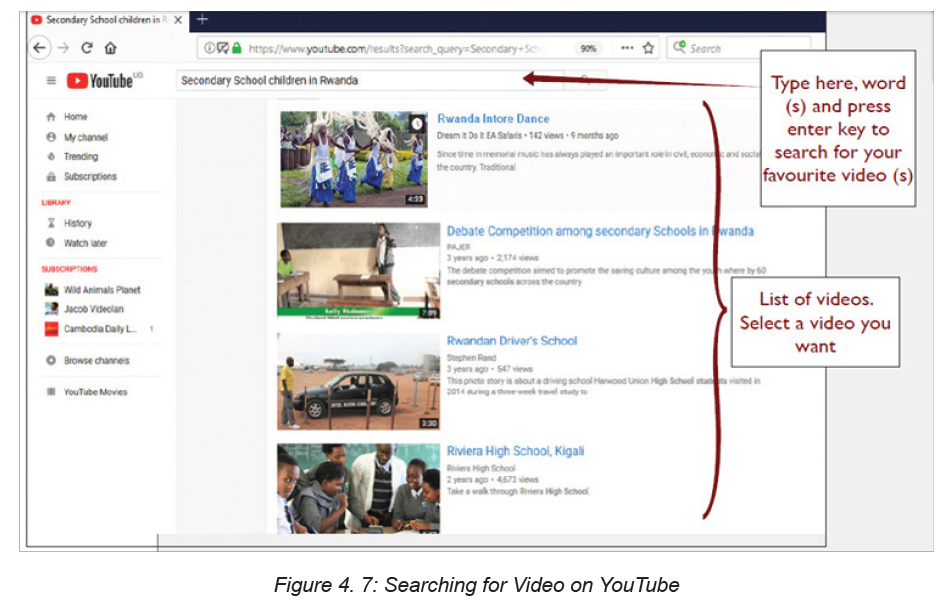
different appropriate software such as YTD Video Downloader, Internet Download
Manager so that they can be watched offline.
D.3. Searching for images and videos on internet using add-on software
• Software add-on
This is a piece of software that adds a specific feature or capability to an existing
software application. A software add-on cannot be run independently; it is just a
software extension.
Examples of common add-ons are Adobe Flash, QuickTime, Download Helper and
Silverlight.
• Download Helper
This is a tool used to extract videos and image files from websites and save them
to the hard drive.
• Download file (Video) using add-ons/download helper
Type in the Address bar “www.YouTube.com”. Locate a favorite video and click
on it.
To download a video on YouTube, there is a red button under Active Video download.
If Download Helper is used and there is an active video on any website, the icon isactive for downloading it, see the figure below.
Click the above Download button of the active video then Save As dialog box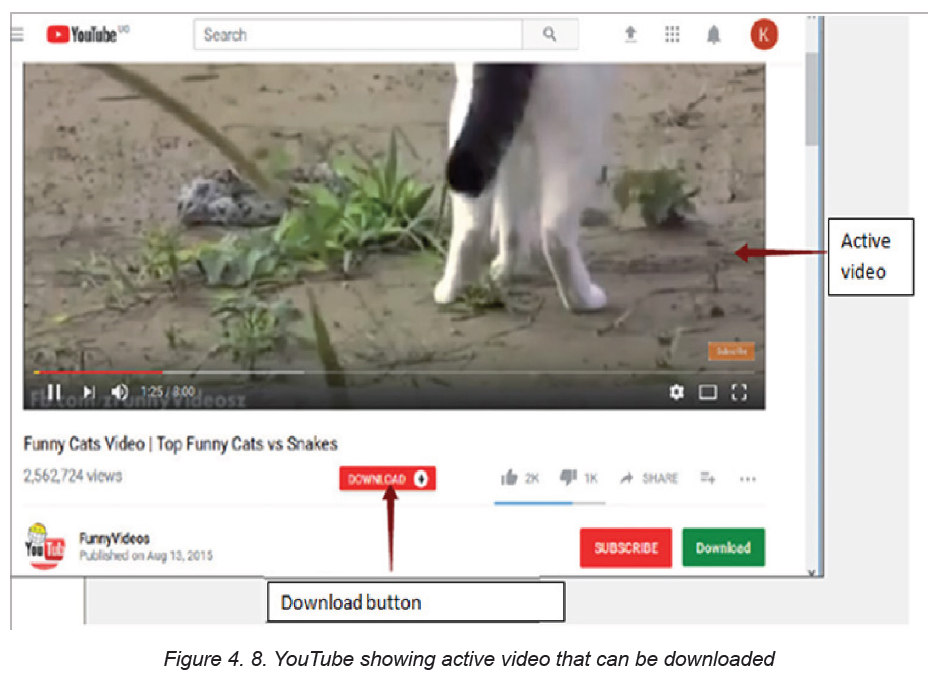
is displayed and at this stage user can select the location where to save the
downloaded video.
Note: YouTube has been designed for users who only watch and view videos on
their website. In case to save the video on computer is needed, select from a variety
of online downloader programs to download the video.
APPLICATION ACTIVITY 4.5
1. a) Through the use of internet and by using different techniques, search for
a video on any one of the three video hosting services (YouTube, Vmeo,
Twitch). The video to search for is about “grain germination”
b) Which one gives more related search results? Explain
2. Search on internet a book called “Imigani miremire ” written by Aloys
BIGIRUMWAMI
3. Create a folder on Desktop and call it your name, thereafter Search on
internet the current map of Rwanda and save it in the created folder
Take an image of your classmates in the classroom and save it on the computer
with internet connectivity. Using that saved image search for similar images of
students (or student teachers) in the classroom.
4.4.2 Searching by image
Activity 4.7
The term search by image also called “reverse photo lookup” is a type of online
search where, user instead of typing in a text-based keyword also known as search
query, uploads an image to find visually similar images and relevant details about
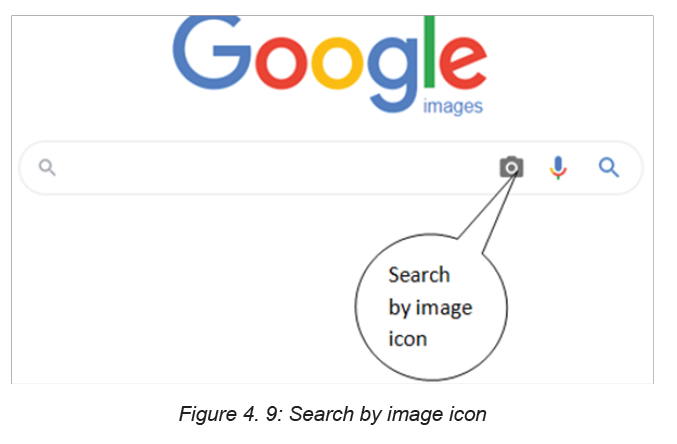
the query image. Here below are procedures to conduct the search by image:
1. Open Google Images (images.google.com)2. Click on the camera icon in the search box.
3. Click Upload an image.
1. Click Choose file’ and browse through the image from PC.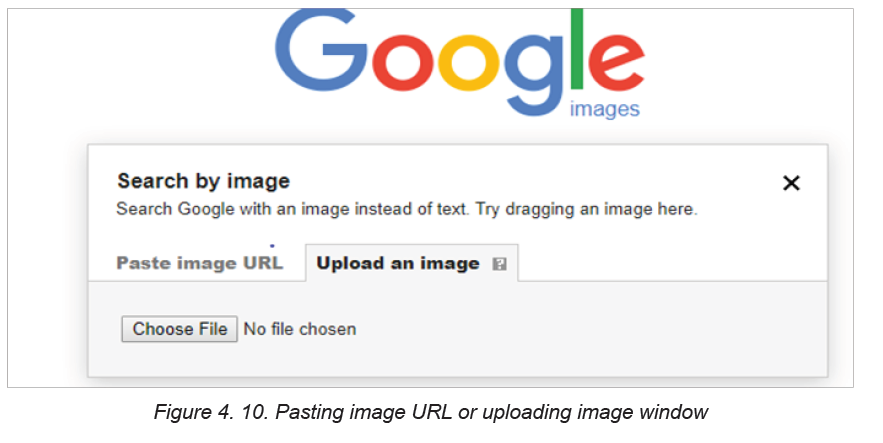
2. Select the image and upload it to Google image.
In the figure above images can be searched by pasting the address (Paste image
URL) of searched image or by uploading it. The term upload has been seen earlier.
Here below is the description of the downloaded image called download33. Theimage shows that it is related to images describing the smart classroom.
APPLICATION ACTIVITY 4.7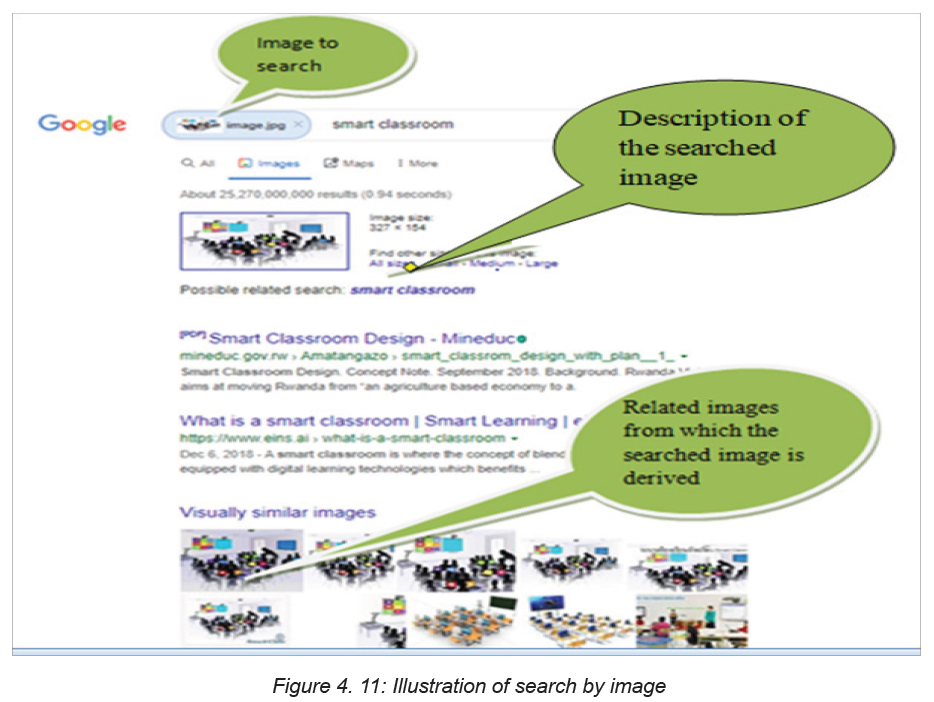
Download ICT books for your subject available on the internet and save them on
your computer.
4.5. Browser’s techniques for remembering
Activity 4.83. What is the role of the cord found in the book below
2. Tom Likes watching movies related to Surgical Pathology on YouTube.
Whenever he opens YouTube he finds Surgical Pathology related topics
displayed the first. For his friend Kamana who likes to watch videos on
History of Rwanda, videos on Surgical Pathology are not displayed.
Discuss the possible reason for this.
People who use the internet testify that the internet seems to be intelligent based on
the feedback and suggestions they get from it. Some websites offer the possibilities
to store some data like details of a filled form, user name and passwords in such a
way that on the next visit to the same website those data won’t need to be refilled.
Some websites like YouTube, social media websites and e-commerce websites
provide suggestions to their visitors depending on their experience for the last visit
on the same website. The different mechanisms through which this is achieved are
elaborated in this topic.
A. Cookies
Cookies are small files which are stored on a user’s computer. They are designed
to hold a modest amount of data specific to a particular client and website and can
be accessed either by the web server or the client computer.
A computer cookie consists of information. When user visits a website, the website
sends the cookie to the computer. The computer stores it in a file located inside the
web browser of the used computer.
The purpose of the computer cookie is to help the website keep track of user visitsand different activities carried out by the users
♦ Some activities of cookies
• Registering which people have visited what pages on a website. This
information can then be used to choose the right advertisement or otherwise
tailoring the pages the user may view. Many cookies used for advertising and
tailoring content are third-party cookies.
• Monitoring the traffic through statistics to improve the site and learn more
about different target groups.
• Keeping track of the selected language.
♦ Where to locate, enable or delete cookies
1. Open the browser. Because cookies are stored in the web browser, the first
step is to open the browser.
2. Find where cookies are stored. Each browser manages cookies in a different
location.
For example, in Internet Explorer, find them by clicking “Tools” and then Settings.
And then click advanced settings”
In Chrome, choose “Preferences” from the Chrome menu in the navigation bar,
display settings. Then expand the “Advanced” option to display “Privacy and
security.” From there, open “Content settings” and “Cookies.”
1. Manage the cookies. Every browser gives a range of options for enabling
or deleting cookies. Internet Explorer for instance, allows managing cookies
under “Privacy” and “Advanced.” In Chrome, find where cookies are stored
as outlined above, and then select the management options under “Cookies.”
B. Bookmark
When referring to an Internet browser, a bookmark or electronic bookmark is a
method of saving a web page’s address. In Microsoft Internet Explorer, bookmarks
are referred to as favorites.
♦ The purpose of bookmark
A bookmark is very useful when user finds a webpage that should be remembered
in order to be able to look at it another day. Bookmarking is like creating a shortcut
for quick access to that web page.
Here below is a list of shortcuts that can be used to access and view the bookmarks
in a browser:
• Google Chrome: Ctrl+Shift+O• Mozilla Firefox: Ctrl+B or Ctrl+ Shift+B
• Microsoft Edge: Ctrl+I
• Internet Explorer: Ctrl+I
• Opera: Ctrl+Shift+B
♦ Process of viewing bookmark in Google chrome
1. Open the Google Chrome browser.2. Navigate to the page to bookmark.
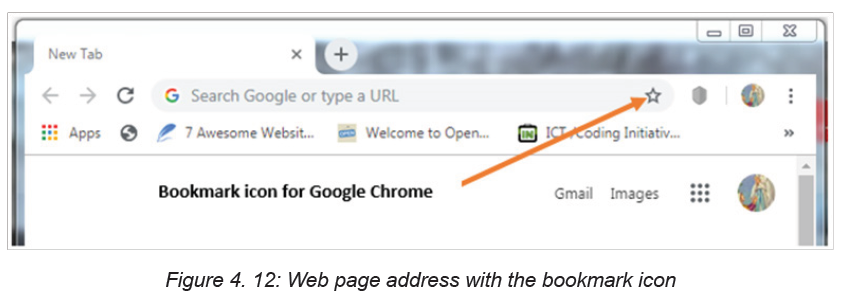
3. Press Ctrl+D or click the star icon on the far side of the address bar
d. Cache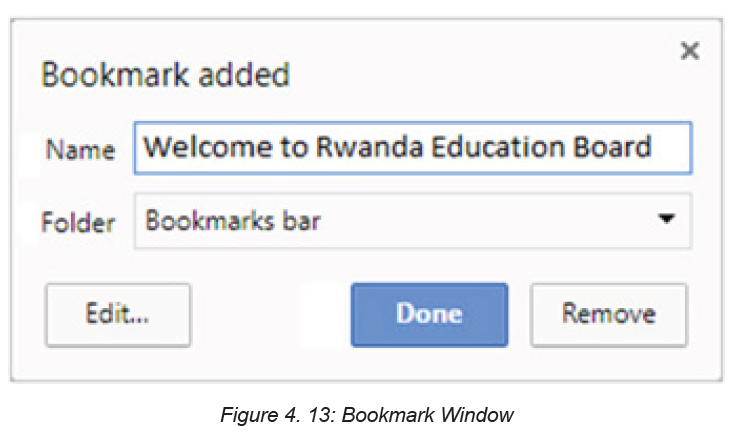
A web cache also known as a HTTP cache or page cache is a system that temporarily
stores data such as web pages, images and similar media content when a web
page is loaded for the first time.
When a user visits a page for the first time, a site cache commits selected content
to memory and when that same page is visited again, the site cache is able to recall
the same content and reload it much quicker when compared to the first visit.
e. Browser history
In computing system, the term web browsing history refers to a list of web pages
a user has visited recently and associated data such as page title and time of visit
which is recorded by the web browser software as standard for a certain period
of time. Web browsers software do this in order to provide the user with a back
button and a history list to go back to pages they have visited previously as well as
displaying visited links
which is recorded by the web browser software as standard for a certain period
of time. Web browsers software do this in order to provide the user with a back
button and a history list to go back to pages they have visited previously as well as
displaying visited links
Viewing browsing history in Google Chrome:
All web browsers keep a record of every page visited in their web history. Here are
the steps followed to view a browser’s history:
1. Open the browser.
2. Click the icon located to the far-right corner of Google Chrome under the
closing icon.
3. Select History. This option is near the top of the drop-down menu. ...
4. Click History. It’s at the top of the pop-out menu.5. Review the browsing history
APPLICATION ACTIVITY 4.8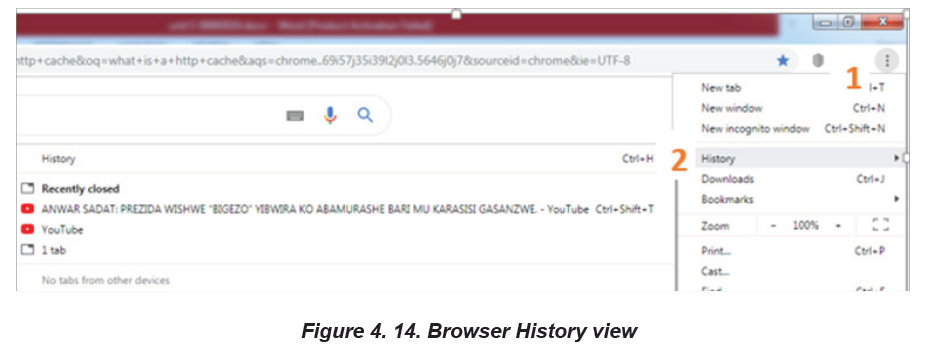
1. Explain the purpose of Bookmark, cookies Cache.
2. Using internet explain three ways to view bookmarks using differentbrowsers.
End unit assessment
1. What is URL? Explain the five parts of URL
2. What does the prefix https:// in a browser address field mean?
3. Differentiate web page from web site
4. When moving from one web page to another, it is a good to open each web
page in a different window. Try opening the following links, each in its own
window: www.igihe.com, www.reb.rw, www. google.com
5. What is a browser’s page history? What is its purpose?
6. Define the term search engine and list at least three examples of the most
common ones
7. Nowadays most services are carried out online by using the web
application www.irembo.gov.rw. With your computer connected to Internet,
search for steps to be followed while applying for National ID using thisweb application.
BIOGRAPHY
1) National Curriculum Development Centre (NCDC). (2011). ICT Syllabus for
Upper Secondary. Kigali.
2) MYICT. (2011). National ICT strategy and plan NICI III-2015.Kigali.
3) National Curriculum Development Centre (NCDC). (2006). ICT syllabus for
Lower Secondary Education. Kigali.
4) Pearson Education. (2010). Computer Concepts.
5) Rwanda Education Board (REB), (2019), ICT Syllabus for TTC, (2019),
Kigali
6) Rwanda Education Board (REB) (2019), Computer Science S5 student’s
book
7) Rwanda Education Board (REB) (2019), Computer Science S6 student’s
book
8) Rwanda Education Board (REB) (2019), Information and Communication
Technology for Rwandan Schools Secondary 1 Students’ Book
9) Rwanda Education Board (REB) (2019), Information and Communication
Technology for Rwandan Schools Secondary 1 Students’ Book
10) Rwanda Education Board (REB) (2019), Information and Communication
Technology for Rwandan Schools Secondary 2 Students’ Book
11) Longhorn Publishers (2016) Computer Science For Rwandan Schools
Senior Four Student’s Book
12) Fountain Publishers (2016) Information and Communication Technology(ICT) for Rwanda Schools Learner’s Book Senior Three
